Welcome to our website and course on how to create a secure phone. Our goal is to help you regain your freedom and privacy by providing you with information and options about how to create your own secure phone.
Why Current Phone Options are a Dangerous Trap
Like candy offered to children, our cell phones lure us into a trap. While they help us keep in touch with our friends, they also rob us of our privacy, our data and our freedom. We become slaves to a system that most of us would bitterly oppose – if only we knew the truth about the harm that these candy phones inflict on us, on our friends, our family and our children.
So called Smart Phones are little more than spying devices. Thanks to the presence of built in back doors, their microphones and cameras can be remotely turned on and forced to stay on even when you turn them off.
Google is not your friend… and neither is Apple!
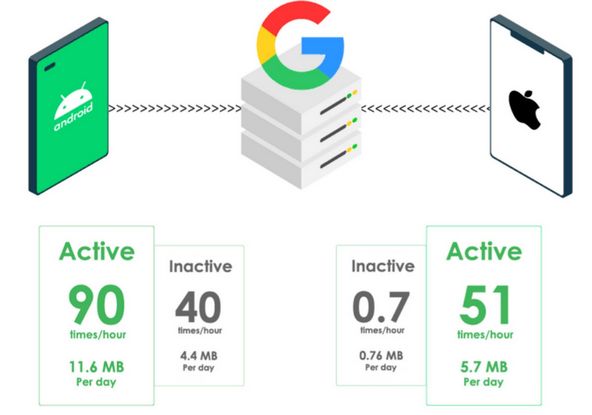
Google is a Deep State corporation that is worth about a trillion dollars. Google makes its money by gathering user information and then selling your information to other corporations. Research has confirmed that Android phones call home to their mother ship 90 times an hour – more than once a minute. Apple phones also call home to their mother ship about once a minute.
Edward Snowden urged folks to put tape over their cell phone cameras and pull out the battery. Here is what he had to say about Android and Apple: Both Android and Apple phones are not very good at protecting your Privacy. What they are selling is not information. What they are selling is us. They are selling our future. They are selling our past. They are selling our history. Our identity. Ultimately, they are stealing our power. Hackers including the government will try to remotely take over your device. Once they control your device, they can read your emails, they can collect your documents, they can look at your contacts. They can turn location services on. They can turn on your camera and your mic. The screen may be off as it is sitting on your desk. But the device is talking all of the time. Once your phone is hacked, what is in their hands is not merely your device, it is your future. - Edward Snowden March 2021
The CIA even uses cell phone GPS transmissions to target and kill people – all too often the wrong people! When Donald Trump became President of the US, there was a major debate because he insisted on continuing to use his Android phone. Cell phones are a Hacker Heaven – but a nightmare for anyone needing privacy and or security. Sadly, most do not see the harm. They suffer from Stockholm syndrome where they become dependent on their oppressors.
But some do see the harm. Some have been seeking other options for many years. Some have an urgent need for a secure phone. This includes newspaper reporters, doctors, lawyers and political activists. The problem is that until recently, fully secure phones did not exist.
What is real phone security?
There is now a huge market in cell phone covers.

This of course, still leaves on your cell phone microphone. But equally important, all of your credit card passwords, text messages, emails, browsing history and web searches are exposed because the operating systems of cell phones also have deliberate back doors hidden in them. This is because both Google (Android) and Apple (iphone) are “Prism Partners” of active partners of what some people call the Deep State. This brings us to our first point: If your cell phone is not using the Linux operating system, it is not a secure phone.
Android is not Linux
Android is Google with a friendly mask. Google makes the Android operating system. Android is supposedly an open source operating system based on a modified version of the Linux kernel. In fact, the actual version of Android running on an Android phone is not open source and can not run real Linux applications. Instead, Android by design only runs Android applications – making Android a vertical monopoly controlled entirely by Google.
There are many groups that claim they can “degoogle” or “ungoogle” Android and still run Android Apps – thus allowing users to maintain their addiction to Android and pretend to have a secure phone. All of these claims are ridiculous. They fail to understand the interdependence of Android and Android apps.
Google adds a bunch of code to Android called scripts or libraries. Android Apps in turn require these Android libraries to run. This is why Android apps will not run on Linux and why Linux apps will not run on Android. Real Linux apps do not need to include Android Libraries.
There are some groups who are so addicted to Android apps that they have made versions of Android apps that will run on a real Linux phone. However, they do this by adding back the Android AKA Google libraries to their programs – thus defeating the entire purpose of creating a secure Linux phone.
I therefore do not recommend running Android apps on your Pinephone Pro. Android apps are as insecure as the Android operating system. It is much better and much safer to replace insecure Android Apps with secure Linux apps just as it is much safer to replace insecure Windows apps with secure Linux apps instead of trying to run insecure Windows programs on Linux.
If you think I am exaggerating, just take a closer look at the Android Logo. Even the letters in the word Android have been dehumanized.
Current Linux Phone Options
Currently, the most secure Linux phone in existence is the Purism Librem 5.
This phone comes with the Pure Operating System which is based on the Linux Debian operating system. It also includes the Phosh Mobile Display – based on the Gnome Display Environment – also called a Graphical Shell (Phosh stands for Phone Shell). Here is a link to more information about this remarkable Linux phone: https://puri.sm/products/librem-5/
There are however two major problems with this phone. The first is that the standard version is nearly impossible to get. Many have waited more than a year to get one of these phones. The second problem is cost. The standard version costs $1300. A version made in the US with a four week wait period costs $2000. These prices are beyond the reach of many people.
Therefore, in this course, we will focus on a much less expensive phone called the Pinephone Pro – which is currently available and only costs $400. Here is an image of the Pinephone Pro:
In some ways, the Pinephone Pro is even better than the Purism Librem 5. For example, it has 4 GB of RAM where the Librem 5 has 3 GB of RAM. In addition, there are entire communities of people developing software for the Pinephone Pro. We will look at some of these software options in a moment. Here is a link to the Pinephone Pro website:
https://www.pine64.org/pinephonepro/
The Importance of Convergence
Unlike the duopoly privacy robbing cell phones, the Pinephone Pro is much more that just a secure cell phone. It is also a real computer – but just made in the shape of a cell phone. This means that when combined with a docking station, it can be hooked up to a monitor, keyboard and mouse to create a working desktop computer!
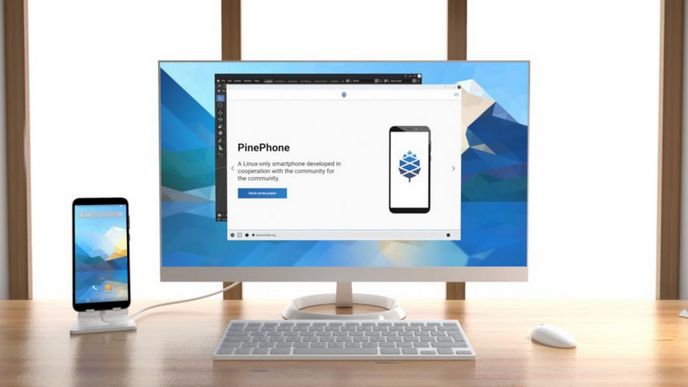
What makes this possible are recent major advances in dual purpose operating systems and applications that display well on both small cellphone screens and large desktop monitors. This concept is called Convergence. It has been the dream of many people for many years. The Pinephone Pro makes this possible by having a much faster processor than the previous model, called the Pinephone. The Pinephone Pro also has 4 GB of RAM – making it capable of running almost any modern program.
There are currently at least five “convergent” Linux operating systems. These are Pure OS, Mobian OS (based on Debian OS), Post Market OS – based on Alpine OS, Manjaro OS based on Arch OS and Arch OS. All of these operating systems are intended to be used on ARM processors common with cell phones.
To make matters even more confusing, there are two Display Environments available. These are Phosh DE created by Purism and Plasma Mobile – created by the KDE team. As noted above, Phosh is based in part on the Gnome Display Environment. Pure OS, Mobian and Post Market OS use the Phosh DE. Arch and Manjaro use both the Phosh and KDE Plasma Mobile Display Environments.
The Pinebook Pro comes with the Manjaro OS and Plasma Mobile combination. However, the Pinebook Pro also has a slot to insert a MicroSD card. You can put any operating system you want on that card. In this course, we will review how to put the Manjaro OS Phosh DE combination on a fast MicroSD card. We recommend Manjaro OS because it is better able to install additional programs that any of the other options. We recommend Phosh because it is faster and has better display layouts in many cases when compared to Plasma mobile. This makes Manjaro with Phosh the best option for those wanting to set up a convergent system.

Real Security is based on Transparency
It is important to know how products you depend on are developed. Phones are a combination of hardware and software. To have trust in your phone, you need to know what is inside of the phone and how it was developed. A key benefit of the Pinephone Pro is that both the hardware and software were developed not in secret by a giant corporation but out in the open by an entire community of users.
Pinephone Pro Hardware Transparency
God only knows what is in a Samsung Android phone. The development of the Samsung phone certainly required close coordination between Samsung and Google. All of this development occurred in secrecy. We should not trust Samsung or Google. Neither has a very good track record in terms of protecting your privacy. However, we can and do know what is the hardware is in an Android phone. This is because the Pinephone Pro is built in a simple ARM structure commonly called a Raspberry Pi Single Board Computer. The makers of the Pinephone Pro, called Pine 64 essentially got their start making improved versions of the Raspberry Pi. These improvements eventually led to the Pinebook Pro laptop – a real Linux laptop where you can see and even take apart all of the internal components. The Pinebook Pro eventually led to the Pinephone Pro phone – which is essentially a Pinebook Pro in the shape of a phone instead of being in the shape of a laptop.
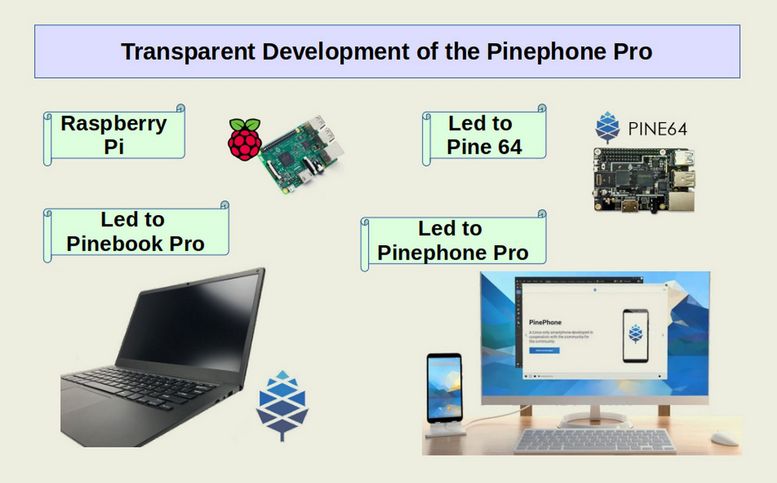
Thus, the Pinephone Pro is not just a mobile phone. It is a real Linux computer that can run Linux applications in the same way that the Pinebook Pro is a Linux computer that can run Linux applications.
Pinephone Pro Software Transparency
The operating system we will review in this course is called Manjaro Phosh. It is a combination of the Manjaro ARM operating system and the Phosh Display Environment developed by Purism. The Phosh Display Environment is based on the Gnome Shell Display Environment. In addition, Manjaro is based on Arch Linux, one of the most freedom respecting Linux operating systems.
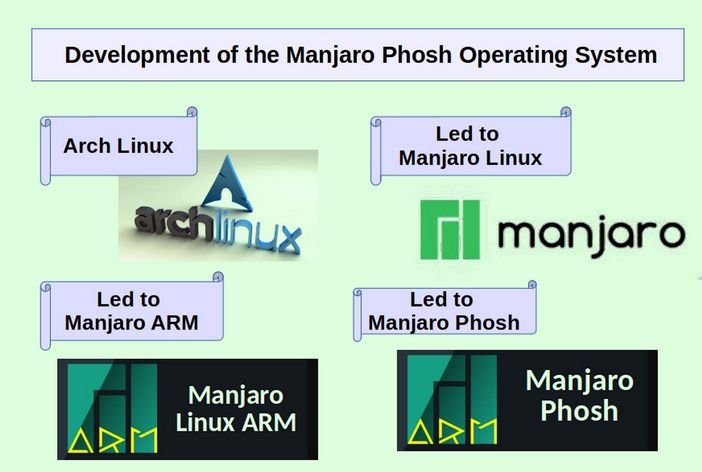
Thus while Android and Apple phones were developed in secret by massive corporations with a long record of cooperation with the Deep State, the Pinephone Pro hardware and software were developed out in the open.
What’s Next?
The ability to add extra programs is one of the most overlooked factors when choosing a mobile operating system. Therefore, in our next article, we will provide a summary of these extra programs. We will then explain how to create a Manjaro with Phosh MicroSD card and install it onto your Pinephone Pro.

